Hey Folks welcome to my blog. A user of our { Xtreme Pentesting }. Requested information on this topic, and i thought it will be nice to write about some good topics like this. So let's talk about our topic without wasting a bit.
📡 HTTP
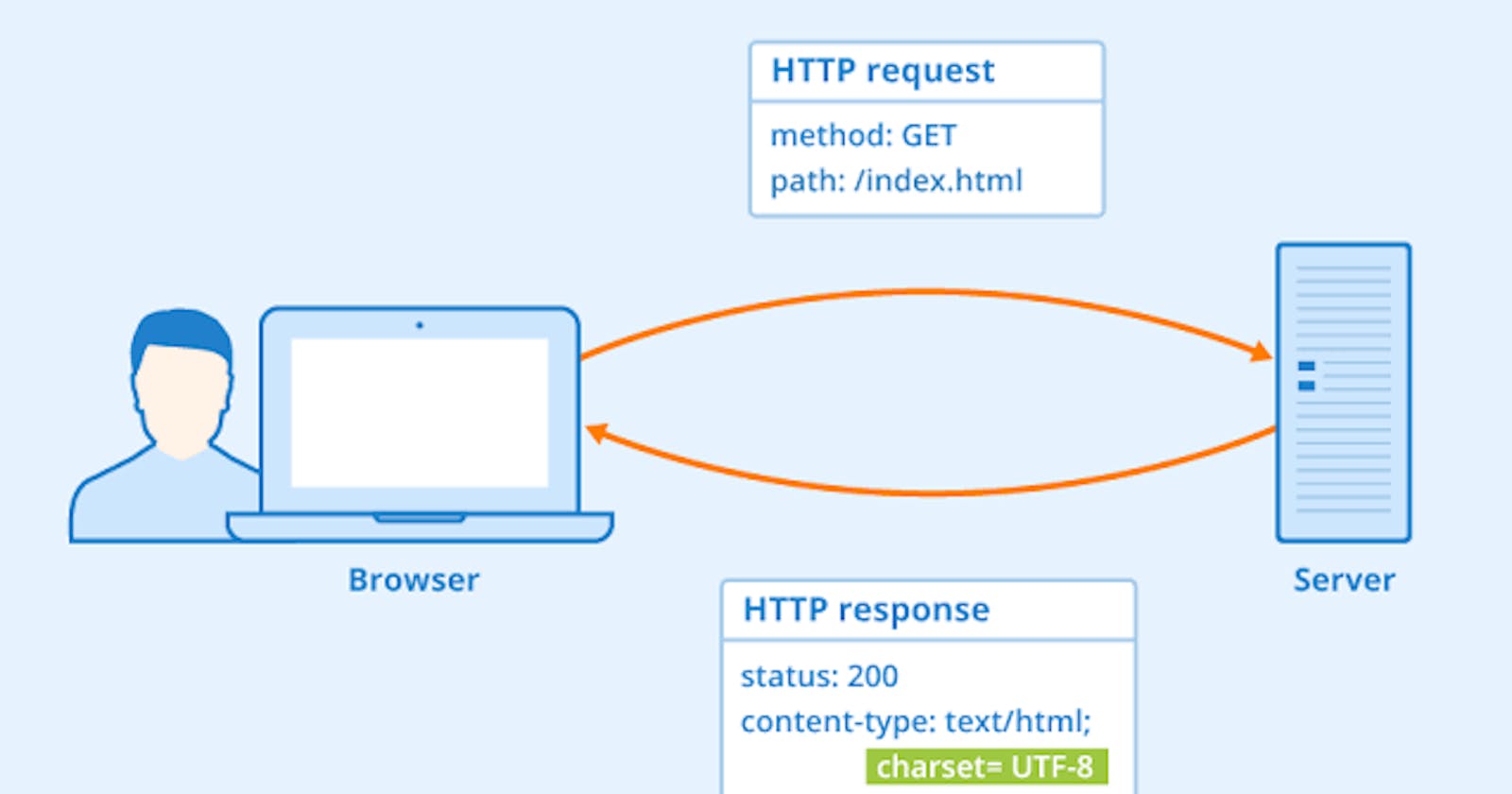
It stands for " Hyper Text Transfer Protocol ". It's an protocol which allows fetching resources over web such as html.
It's a Client Server Architecture requests are sent by one entity, the user-agent (or a proxy on behalf of it). Most of the time the user-agent is a Web browser, but it can be anything, for example a robot that crawls the Web to populate and maintain a search engine index (google bot) .
Each individual request is sent to a server, which handles it and provides an answer, called the response.
♨️ HTTP Headers
Headers are name/value pairs that appear in both request(client) and response(web server) messages. The name of the header is separated from the value by a single colon. For example, this line in a request message:
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; rv:11.0) like Gecko
provides a header called User-Agent whose value is Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1). The purpose of this particular header is to supply the web server with information about the type of browser making the request.
⭕ Roles of these headers
These headers let client and server pass additional information with an HTTP Request or Response .
☢️ HTTP Headers and Website Security
List of basic web security headers :
# HSTS
# CSP
# X-Frame-Options
# XSS Protection
# X-Content-Type-Options
# Referrer-Policy
# Cache Control
(1) Strict-Transport-Security When enabled on the server, HTTP Strict Transport Security (HSTS) enforces the use of encrypted HTTPS connections instead of plain-text HTTP which is more secure compared to HTTP communication. An example of HSTS header:
Strict-Transport-Security: max-age=63072000;
includeSubDomains; preload
This would inform the visiting web browser that the current site (including subdomains) is HTTPS-only and the browser should access it over HTTPS for the next 2 years (the max-age value in seconds). The preload directive indicates that the site is present on a global list of HTTPS-only sites. Preloading is intended to speed up page loads and eliminate the risk of man-in-the-middle (MITM) attacks when a site is visited for the first time.
(2) Content-Security-Policy(CSP)
This header is very important for an XSS Scenario and it protects website or webapp against XSS Attacks. Here’s an example policy HTTP header to allow assets (scripts, CSS, fonts, images, etc.) only from the default source, which is the same origin ('self').
Content-Security-Policy: default-src 'self'
(3) X-Frame-Options
The X-Frame-Options header enables you to specify whether or not a browser should be allowed to render a page in a frame, iframe, or object as follows:
DENY: Page cannot be displayed in a frame.
SAMEORIGIN: (The default Magento setting.) Page can be displayed only in a frame on the same origin as the page itself.
(4) XSS Protection
The X-XSS-Protection header is designed to enable the cross-site scripting (XSS) filter built into modern web browsers. This is usually enabled by default, but using it will enforce it. It is supported by Internet Explorer 8+, Chrome, and Safari. The recommended configuration is to set this header to the following value, which will enable the XSS protection and instruct the browser to block the response in the event that a malicious script has been inserted from user input, instead of sanitizing.
X-XSS-Protection: 1; mode=block
(5) X-Content-Type-Options
The HTTP headers X-Content-Type-Options acts as a marker that indicates the MIME-types headers in the content types headers should not be changed to the server. This header was introduced in the Internet Explorer 8 of Microsoft. This header block the content sniffing (non-executable MIME type into executable MIME type). After that, all the other browsers also introduce the X-Content-Type-Options, and their MIME sniffing algorithms were less aggressive.
x-content-type-options: nosniff
(6) Referrer-Policy
The Referrer-Policy HTTP header controls how much referrer information (sent via the Referer header) should be included with requests.
Referrer Policy options
No-referrer — No referrer information is sent.
No-referrer-when-downgrade — This is the default behavior if no policy is specified. It always passes the full path and will pass a value from HTTPS > HTTPS but not HTTPS > HTTP.
Origin — Sends the domain but not the full path.
Origin-when-cross-origin — Sends the full path when on the same domain, but only the domain when passing to another website.
Same-origin — Sends the full path if it’s the same domain, but strips the value if going to another website.
Strict-origin — Sends the domain for HTTPS > HTTPS and HTTP > HTTP, but not HTTPS > HTTP.
Strict-origin-when-cross-origin — Sends the full path if on the same domain and from one secure page to another, sends the domain if going from HTTPS on one domain to another domain, and doesn’t pass if going from a secure domain to an insecure domain.
Unsafe-url — Sends the full path.
(7) Cache Control
Cache-control is an HTTP header used to specify browser caching policies in both client requests and server responses. Policies include how a resource is cached, where it’s cached and its maximum age before expiring.
Cache-Control: no-store
Cache-Control: no-cache
Cache-Control: private
Cache-Control: public
Cache-Control: max-age=31536000
Cache-Control: must-revalidate
Thanks For Reading. Kindly comment out mistakes and any suggestions, list isn't complete yet I didn't wanted to make it long so gave a brief description.
Hope You Guys Like It